With LIMS’ Configuration Manager you can configure the system to work exactly the way you want it to.
If you add a new line of business, simply define its business rules in the Configuration Manager, and you have an information system to support your new business activities — without additional systems development work!
Establish the company, division and report hierarchies
You can define name and defaults for your company and divisions that apply throughout the system
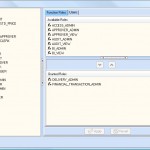
Assign security levels for the entire system and for each individual user
Security features in LIMS allow authorized users to access information and functionality, providing a well-secured environment. During your implementation project, the prime user (for example a manager, controller or director) defines the access rules use for each type of user, and assigns individual users to security groups.
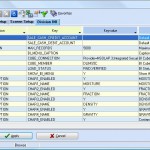
Define corporate information
This module allows you to set up information about your scales, yards and decks, divisions, and so on. You also define the codes and their meanings you want LIMS to use
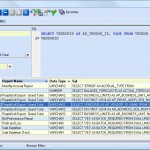
Customize LIMS
You can fully customize LIMS to match your business rules, conventions, and terminology. Menu items can be added, renamed, and deleted. Rules for contracts, audit, jobs, exceptions, etc., can also be set up in the Configuration Manager.
Faster information gathering and processing
Camps and remote operations are connected to the central LIMS system so information can be tracked in the bush and at the mill and be accessible from head office immediately.
Shorter set-up time
The Configuration Manager module minimizes your set-up time by allowing you to continue using your existing financial software and business codes. This saves much of the time needed to configure the system at initial implementation.
Information security
The level of use can be set in the Configuration Manager module for each user. Data access is also controlled at the database level, so no information can be obtained without the proper authentication. This protects your company’s most valuable asset — information.